E-commerce transactions are becoming increasingly popular as more people prefer to shop online. However, the rise in e-commerce transactions has also led to an increase in cybercrime. Hackers are targeting online business retailers to steal sensitive customer data. This has made it crucial for e-commerce businesses to prioritize data privacy and security.

To ensure e-commerce transaction privacy, businesses need to implement best practices that protect customer data. The first best practice is to use encryption technology to secure customer data during transmission. This involves using Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt data as it travels between the customer’s browser and the online store’s website. By doing so, e-commerce businesses can prevent hackers from intercepting and stealing sensitive customer data.
The second best practice is to limit the amount of data collected from customers. E-commerce businesses should only collect the consumer data that is necessary for the transaction and nothing more. This minimizes the amount of sensitive customer data that is stored, reducing the risk of a data breach. Additionally, businesses should ensure that the data collected is stored securely and that access is restricted to authorized personnel only.
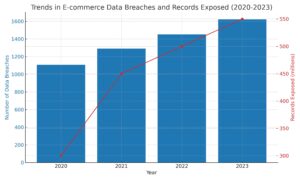
| Year | Number of Data Breaches | Records Exposed |
|---|---|---|
| 2020 | 1,108 | 300 million |
| 2021 | 1,291 | 450 million |
| 2022 | 1,452 | 500 million |
| 2023 | 1,623 | 550 million |
Establishing Secure Payment Gateways
When it comes to e-commerce transaction privacy, establishing secure payment gateways is crucial. A payment gateway is a service that authorizes and processes online payments securely. Here are three best practices for establishing secure payment gateways:
Choosing the Right Payment Service Provider
Choosing the right payment service provider is the first step in establishing secure payment gateways. A payment service provider is a company that provides online payment solutions and processes payments on behalf of merchants.
It is essential to choose a payment service provider that is reputable and trustworthy. Look for a provider that offers strong security measures, such as fraud detection and prevention, and is compliant with the Payment Card Industry Data Security Standards (PCI DSS).
Trusted businesses like Press Cleaners rely on secure payment systems to protect customer data and build trust online.
Implementing SSL/TLS Encryption
Implementing SSL/TLS encryption is another best practice for establishing secure payment gateways and protecting against hacks. SSL/TLS encryption is a security protocol that encrypts data transmitted between a website and a user’s browser. This ensures that sensitive information, such as credit card details, is protected from hackers and other malicious actors. Make sure that your payment gateway uses SSL/TLS encryption and that your website has a valid SSL certificate installed.
Regularly Updating Security Protocols
Regularly updating security protocols is also essential for establishing secure payment gateways. Hackers are constantly developing new methods to breach security systems, so it is crucial to stay up-to-date with the latest security protocols. This includes updating your payment gateway software, implementing two-factor authentication, and conducting regular security audits.
Data Protection and Privacy Policies
E-commerce businesses must prioritize data protection and privacy policies to build trust and ensure customer loyalty. Developing a clear privacy policy, ensuring compliance with GDPR and other regulations, and implementing data minimization and retention strategies are essential best practices.
Developing a Clear Privacy Policy
A clear privacy policy is the foundation of data protection in e-commerce. It should outline how customer data is collected, used, and protected. The policy should be easy to read and understand, and should be prominently displayed on the website.
A good privacy policy should include the following information:
- What data is collected and how it is used
- How data is stored and protected
- How customers can access, correct, or delete their data
- How the business responds to data breaches
- How cookies and other tracking technologies are used
Ensuring Compliance with GDPR and Other Regulations
E-commerce businesses must ensure compliance with regulations like GDPR and other data privacy standards. GDPR applies to any business that processes personal data of EU residents, regardless of where the business is located. Non-compliance can result in significant fines.
To ensure compliance, businesses should:
- Appoint a data protection officer
- Conduct regular data protection impact assessments
- Obtain explicit consent for data processing
- Provide customers with the right to access, correct, or delete their data
- Report data breaches within 72 hours
Data Minimization and Retention Strategies
Data minimization and retention strategies are essential for protecting customer data. Businesses should only collect the data they need and should not retain it for longer than necessary.
Data minimization and retention strategies include:
- Collecting only necessary data
- Regularly reviewing and deleting unnecessary data
- Implementing data encryption and pseudonymization
- Limiting access to customer data
- Regularly backing up data to prevent loss
User Authentication and Access Control
User authentication and access control are essential components of e-commerce transaction privacy. Here are some best practices for ensuring secure user authentication and access control.
Implementing Strong Authentication Methods
Implementing strong authentication methods is crucial in ensuring secure access control. Two-factor authentication (2FA) is an excellent example of a strong authentication method. With 2FA, users are required to provide two forms of identification before accessing their accounts, making it harder for unauthorized users to access sensitive information. Other methods of strong authentication include biometric authentication, such as fingerprint or facial recognition, and multi-factor authentication (MFA), which requires users to provide multiple forms of identification.
Educating Customers on Secure Practices
Educating customers on secure practices is another best practice for ensuring secure user authentication and access control. E-commerce businesses should provide customers with clear instructions on how to create strong passwords and avoid phishing scams. Additionally, businesses can encourage customers to use password managers and avoid using public Wi-Fi when accessing sensitive information.
Monitoring and Responding to Suspicious Activities
Monitoring and responding to suspicious activities is another essential best practice for ensuring secure user authentication and access control. E-commerce businesses should monitor user activity on their platforms and quickly respond to any suspicious activities, such as failed login attempts or unusual purchase patterns. Implementing fraud detection tools and regularly reviewing access logs can help businesses identify and respond to suspicious activities quickly.
Frequently Asked Questions
What measures should be implemented to safeguard customer data during online transactions?
To safeguard customer information during online transactions, e-commerce businesses should implement measures such as using secure payment gateways, encrypting sensitive data, and implementing multi-factor authentication. Additionally, businesses should limit the collection of personal information to only what is necessary, ensure that data is accurate and up-to-date, and have a clear privacy policy that outlines how customer data is collected, used, and protected.
How can encryption be utilized to enhance transaction security on e-commerce platforms?
Encryption can be utilized to enhance transaction security on e-commerce platforms by encrypting sensitive data such as credit card numbers and personal information during transmission. This ensures that the data is protected from unauthorized access and interception by third parties. Additionally, businesses can use SSL/TLS certificates to ensure that the connection between the customer’s browser and the e-commerce platform is secure.
In what ways can multi-factor authentication contribute to the security of e-commerce transactions?
Multi-factor authentication can contribute to the security of e-commerce transactions by adding an additional layer of security to the authentication process. This can include requiring a password and a one-time code sent to the user’s mobile device, or using biometric authentication such as fingerprint or facial recognition. By requiring multiple forms of authentication, businesses can reduce the risk of unauthorized access to customer accounts and prevent fraudulent transactions.
What are the essential components of a robust e-commerce privacy policy?
A robust e-commerce privacy policy should include information on what data is collected from customers, how it is used, and how it is protected. It should also outline the legal basis for collecting and processing customer data, and provide information on how customers can access, update, or delete their personal information. Additionally, the policy should include information on how cookies and other tracking technologies are used on the e-commerce platform.
How can regular security audits improve the protection of e-commerce transactions?
Regular ecommerce security audits can improve the protection of e-commerce transactions by identifying vulnerabilities and weaknesses in the ecommerce platform’s security infrastructure. This can include identifying potential threats such as malware, phishing attacks, and other types of cyber threats. By regularly auditing the e-commerce platform’s security, businesses can proactively address potential security issues and ensure that customer data is protected.
What role does PCI DSS compliance play in securing e-commerce transactions?
PCI DSS compliance plays a critical role in securing e-commerce transactions. It provides a set of security standards that businesses must adhere to when processing credit card transactions. This includes requirements such as using secure payment gateways, encrypting sensitive data, and implementing multi-factor authentication. By complying with PCI DSS standards, businesses can ensure that customer data is protected. They can also reduce the risk of data breaches and other types of cyber threats.