Online privacy is a growing concern in today’s digital age. With the increasing use of digital media, it has become crucial to protect personal information from unauthorized access. Digital Rights Management (DRM) is one such technology that is used to protect digital content from being stolen, shared, and sold illegally. However, it is important to note that DRM does not offer complete protection against privacy breaches. Therefore, it is necessary to adopt best practices for online privacy in DRM.

The first best practice for online privacy in DRM is to be aware of the privacy policies of the DRM provider. It is important to read and understand the privacy policies of the DRM provider before using their services. This will help users to understand how their personal information is being collected, stored, and used by the provider. Additionally, users should ensure that the DRM provider is compliant with the relevant data protection regulations.
The second best practice for online privacy in DRM is to use strong passwords and two-factor authentication. Users should create strong passwords that are difficult to guess and use different passwords for different accounts. Two-factor authentication adds an extra layer of security to the account and makes it difficult for hackers to gain unauthorized access. Users should also avoid sharing their passwords with anyone and regularly change them to prevent unauthorized access.
| Statistic | Value | Description |
|---|---|---|
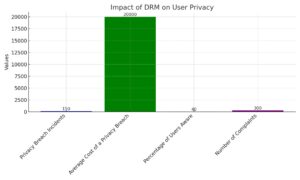
| Privacy Breach Incidents | 150 | Number of reported incidents involving DRM privacy breaches. |
| Average Cost of a Privacy Breach | $20,000 | The average financial impact of a DRM-related privacy breach. |
| Percentage of Users Aware of Privacy Policies | 40% | Percentage of users who understand the privacy terms of DRM. |
| Number of Complaints | 300 | Complaints filed regarding privacy issues with DRM systems. |
Understanding DRM and Its Importance
What Is DRM?
Digital Rights Management (DRM) is a set of technologies and protocols designed to protect digital content from unauthorized access, reproduction, and distribution. It is used to enforce copyright protection, licensing agreements, and access control for various forms of digital media, including music, videos, ebooks, and software. DRM technology is used to encrypt digital assets and control access to them, ensuring that only authorized users can view or use the content.
The Role of DRM in Protecting Digital Content
DRM plays a critical role in protecting digital content from piracy, unauthorized sharing, and theft. DRM technology helps content creators and distributors to control access to their intellectual property, ensuring that only authorized users can view or use the content. DRM technology also helps to prevent unauthorized copying, distribution, and sharing of copyrighted materials, thereby protecting the interests of content creators and distributors.
Benefits of DRM for Content Creators and Distributors
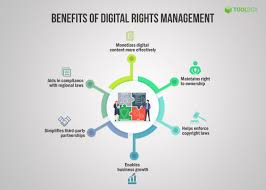
DRM technology offers several benefits to content creators and distributors. First, it helps to protect their intellectual property rights by preventing unauthorized access, reproduction, and distribution of their digital assets. Second, it helps to ensure that they are fairly compensated for their work by controlling access to their content and enforcing licensing agreements. Third, it helps to promote the growth of the digital content industry by providing a secure and reliable platform for the distribution of digital media.
Implementing DRM Effectively
When it comes to implementing digital rights management (DRM) effectively, there are a few best practices that organizations should follow. These practices can help ensure that the DRM solution is secure, compatible, and user-friendly.
Choosing the Right DRM Solution
Choosing the right DRM solution is critical to ensuring that the organization’s sensitive information is protected. When selecting a DRM solution, it is important to consider the specific requirements of the organization, including access controls and platform support.
Organizations should research and choose a suitable DRM technology that aligns with their requirements. They should also consider the level of encryption and decryption that is necessary to protect their data.
Ensuring Compliance and Compatibility
Ensuring compliance and compatibility is another critical aspect of implementing DRM effectively. Organizations must ensure that their DRM solution is compliant with relevant regulations and licensing agreements. They should also ensure that the solution is compatible with the devices and software that their authorized users are using.
To ensure compliance, organizations should work with legal and compliance teams to understand the relevant regulations and ensure that their DRM solution meets those requirements. They should also consider the impact of DRM on user experience and ensure that the solution is user-friendly.
Balancing Security with User Experience
Balancing security with user experience is also important when implementing DRM effectively. While it is critical to protect sensitive information, organizations should also consider the impact of DRM on user experience.
To achieve this balance, organizations should consider implementing DRM software that is user-friendly and easy to use. They should also consider providing training and support to their authorized users to help them understand how to use the DRM solution effectively.
Best Practices for Online Privacy in DRM
Digital Rights Management (DRM) technology provides organizations with the means to protect sensitive information so that only authorized users can access it. However, it is important to also ensure that user data and privacy are protected. Here are three best practices for online privacy in DRM.
Protecting User Data and Privacy
One of the most important aspects of DRM is ensuring that user data and privacy are protected. This can be achieved by using encryption to protect sensitive information, such as user credentials and personal data. It is also important to ensure that analytics and tracking are used responsibly and only for legitimate purposes, such as improving the user experience.
Preventing Unauthorized Access and Distribution
Another key aspect of DRM is preventing unauthorized access and distribution of content. This can be achieved by implementing access control measures, such as requiring authentication and using encryption to protect the decryption key. It is also important to regularly audit and update the DRM system to ensure that it remains secure and up-to-date with the latest security best practices.
Regular Audits and Updates
Finally, regular audits and updates are essential for maintaining the security of the DRM system. This includes conducting regular security audits to identify vulnerabilities and implementing updates to address any security issues that are identified. It is also important to stay up-to-date with the latest security best practices and to continually improve the security of the DRM system over time.
The Future of DRM and Online Privacy
As technology continues to advance, so does the need for digital rights management (DRM) to protect intellectual property. The future of DRM and online privacy will be shaped by emerging technologies, adapting to new forms of digital media consumption, and legal and ethical considerations.
Emerging Technologies in DRM
Blockchain technology is one of the emerging technologies that is expected to play a significant role in DRM. It can be used to create a decentralized content distribution network that can help protect against piracy and unauthorized distribution of digital content. Additionally, blockchain technology can provide a secure and transparent way to manage digital assets.
Digital asset management (DAM) is another technology that is expected to play a role in DRM. DAM systems can help organizations manage and protect their digital assets, including sensitive information and intellectual property.
Adapting to New Forms of Digital Media Consumption
As digital media consumption continues to evolve, DRM must adapt to new forms of consumption. For example, streaming services have become increasingly popular, and DRM must be able to protect against piracy and unauthorized distribution of streamed content.
DRM must also be able to protect against unauthorized access to digital content on mobile devices, such as smartphones and tablets. This requires DRM systems that can detect and prevent unauthorized access to digital content on these devices.
Legal and Ethical Considerations
DRM must also consider legal and ethical considerations. For example, DRM systems must comply with copyright laws and protect the rights of content creators. At the same time, DRM must also respect the privacy rights of users and ensure that personal information is not collected or used without consent.
Additionally, DRM must consider ethical considerations such as the impact on free speech and access to information. DRM systems must balance the need to protect intellectual property with the need to ensure that information is accessible to all.