Data hacks and cybersecurity breaches are becoming increasingly common in today’s digital age. With the rise of online activity and the growing amount of data being stored online, it is more important than ever to have a solid plan in place to recover from a data breach. In the event of a data hack, a clear and effective strategy is essential to minimize the damage and get back on track as quickly as possible.

One of the best strategies for bouncing back from a data breach is to have a comprehensive recovery plan in place. This plan should outline the steps that need to be taken in the event of a security breach, including who is responsible for what tasks and how communication will be handled. By having a clear plan in place, businesses can minimize the impact of a data breach and get back to normal operations as quickly as possible. Another key strategy for bouncing back from a data hack is to focus on data security and cybersecurity measures to prevent future breaches from hackers. This includes implementing strong passwords, regularly updating software and systems, and training employees on best practices for cyber security. By taking proactive measures to prevent future breaches, businesses can reduce the risk of future data hacks and protect their sensitive information.
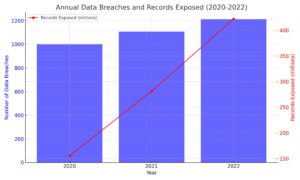
| Year | Number of Data Breaches | Records Exposed |
|---|---|---|
| 2020 | 1,001 | 155.8 million |
| 2021 | 1,108 | 281.5 million |
| 2022 | 1,212 | 422.1 million |
Three Key Steps to Overcome a Data Hacking Incident
Data hacking incidents are a growing concern for businesses of all sizes. In the event of a data breach, it is important to act quickly and effectively to minimize damage and prevent future occurrences. Here are three key steps businesses can take to overcome a data hacking incident:
1. Update Security

The first step in overcoming a data hacking incident is to update security measures. Quickly update software, change passwords, and fix any security vulnerabilities that allow the hacker to gain unauthorized access to the system and deploy ransomware. This will help prevent future attacks and ensure that the system is secure in terms of data security. To strengthen the system further and restrict unauthorized access, additional security measures, such as two-factor authentication, should also be considered.
2. Inform People

The second step is to inform customers and other affected parties about the hack honestly and what steps you are taking to fix the issue. This can help build trust and reassure customers that their data is being protected. It is important to be transparent in your notification about what happened and what is being done to prevent future occurrences.
3. Review and Learn

After handling the immediate issues, it is important to review what happened and why. Use this information to strengthen your system against future attacks. This can include conducting a thorough investigation of the incident, analyzing the compromised data, and identifying any vulnerabilities in the system. It is also important to learn from the incident and implement changes to prevent similar attacks in the future.
Frequently Asked Questions
What steps should a company take immediately after a data breach?
After discovering a data breach, companies should take immediate action to contain it, assess the damage, and promptly alert all stakeholders. This includes identifying the source of the breach, securing all systems to prevent unauthorized access, and notifying any affected parties. It is also important to preserve any evidence of the breach for future investigations.
What are effective methods for improving cybersecurity post-data breach?
To improve cybersecurity post-data breaches, companies should conduct a comprehensive security assessment to identify vulnerabilities and implement appropriate security measures. This may include updating software and systems, implementing multi-factor authentication, and conducting regular security training for employees. It is also important to monitor systems for any signs of suspicious activity and to have a plan in place for responding to future breaches.
How can businesses restore consumer trust following a data breach?
Restoring consumer trust following a data breach requires transparency, accountability, and a commitment to improving security. Companies should be open and honest about the breach and its impact and take steps to mitigate any damage to affected parties. This may include offering credit monitoring or identity theft protection services, and providing regular updates on the status of the investigation and any remediation efforts.
What are the long-term strategies for data breach recovery?
Long-term strategies for data breach recovery include ongoing security assessments and updates, regular employee training, and a commitment to continuous improvement. Companies should also have a plan in place for responding to future breaches, including a clear chain of command and communication plan.
How does one assess the impact of a data breach and mitigate future risks?
Assessing the impact of a data breach requires a thorough investigation of the breach and its impact on systems, data, and affected parties. This may include conducting forensic analysis, reviewing logs and other data, and interviewing employees and other stakeholders. To mitigate future risks, companies should implement appropriate security measures and regularly assess and update their security posture.
What role does employee training play in preventing future data breaches?
Employee training plays a critical role in preventing future data breaches by raising awareness of security risks and best practices. This may include training on identifying phishing scams, creating strong passwords, and reporting suspicious activity. Regular training and reinforcement can help ensure that employees are equipped to identify and respond to potential threats.