Encryption is like turning your secret message into a puzzle. When you send this puzzle to a friend, only they know how to solve it and read your message. Decryption is the solving part. It changes the puzzle back into the message.
Fundamentals of Encryption
Encryption is the process of converting data into a form that is unreadable by unauthorized users. Its purpose is to protect sensitive information such as passwords, credit card numbers, and other confidential data from theft or unauthorized access. Encryption converts the original plaintext into cipher text that can only be read by someone who has the key to decrypt it.
Symmetric vs Asymmetric Encryption
Symmetric encryption uses the same key for both encryption and decryption. The sender and the receiver must have the same key to communicate securely. Symmetric encryption is faster and less complex than asymmetric encryption, but it is less secure because the same key is used for both encryption and decryption.
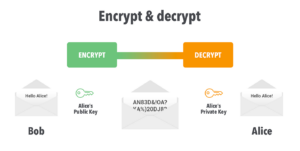
Asymmetric encryption uses two different keys for encryption and decryption. The public key is used for encryption, and the private key is used for decryption. The public key can be shared with anyone, but the private key must be kept secret. Asymmetric encryption is more secure than symmetric encryption, but it is slower and more complex.
Encryption Algorithms Overview

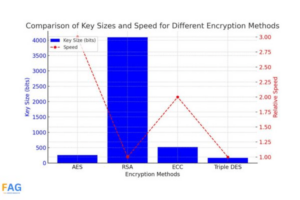
Encryption is a way to protect information by making it unreadable unless you have a special key. There are several types of encryption methods. The Advanced Encryption Standard (AES) is one method used by the U.S. government. Another older method, the Data Encryption Standard (DES), isn’t used much anymore because it’s not as secure. Triple DES improves on DES by using three keys for better security, though it’s slower.
There are two main types of encryption: symmetric and asymmetric. Symmetric encryption uses one key for both locking (encrypting) and unlocking (decrypting) data. Asymmetric encryption uses two keys; a public key to encrypt data and a private key to decrypt it. Encryption keys are like passwords; the longer they are, the harder they are to break. This is how we keep data safe from people who shouldn’t see it.
Implementing Encryption for Data Protection

When it comes to implementing encryption for data protection, there are several best practices that should be followed to ensure that sensitive data is kept secure. The following subsections provide an overview of key management best practices, encryption in different states (at rest and in transit), and advanced encryption techniques.
Key Management Best Practices
Key management is an essential component of the data type of encryption. Encryption keys are used to encrypt and decrypt data, so it is crucial to ensure that they are managed properly. Key management best practices include:
- Regularly rotating encryption keys
- Keeping encryption keys separate from the data they protect
- Storing encryption keys securely
- Using strong encryption algorithms for encryption keys
- Restricting access to encryption keys
Encryption in Different States: At Rest and In Transit
Encryption can be applied to data in two states: at rest and in transit. Data at rest refers to data stored on a device or server, while data in transit refers to data transmitted over a network. Encryption techniques for data at rest include disk encryption and file encryption. Cloud encryption is also becoming increasingly popular as more businesses move their data to the cloud.
Encryption techniques for data in transit include end-to-end encryption (E2EE), which encrypts data as it is transmitted from one device to another. E2EE is becoming increasingly important as more and more communication takes place over the internet. Data encryption tools such as VPNs and SSL/TLS can also be used to encrypt data in transit.
Advanced Encryption Techniques
Advanced encryption techniques are used to provide an additional layer of security for sensitive data. These techniques include:
- Homomorphic encryption: Allows data to be processed while still encrypted, providing an additional layer of security.
- Quantum encryption: Uses quantum mechanics to encrypt data, providing an extremely high level of security.
- Multi-factor authentication: Requires multiple forms of authentication before data can be accessed, providing an additional layer of security.
In conclusion, implementing encryption to prevent data theft is essential for keeping sensitive data secure. By following key management best practices, encrypting data at rest and in transit, and using advanced encryption techniques, businesses can ensure that their data is protected from unauthorized access.
Preventing Unauthorized Access and Maintaining Integrity

Data encryption is an essential security measure that ensures the confidentiality, integrity, and availability of sensitive information. Encryption converts plain text into ciphertext, making it unreadable to anyone who does not have the decryption key. In this section, we will discuss the importance of data encryption types in preventing unauthorized access and maintaining integrity.
Cryptography and Cybersecurity
Cryptography is the science of securing information using codes and ciphers. It is a fundamental component of cybersecurity, protecting data from unauthorized access and ensuring its confidentiality, integrity, and availability. Cryptography techniques include symmetric encryption, asymmetric encryption, and hashing. Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses a public key for encryption and a private key for decryption. Hashing is a one-way function that converts data into a fixed-length string, making it impossible to reverse the process.
Protecting Against Types of Attacks
Data breaches can occur due to various types of attacks, including phishing, ransomware, and malware. Phishing attacks use social engineering techniques to trick users into revealing sensitive information, while ransomware encrypts data and demands payment for its release. Malware is malicious software that can infect a system and steal or delete data. Encryption can protect sensitive data from these types of attacks by making it unreadable to unauthorized users.